Data-signing with Platinum
Platinum systemA "platinum system" is any system running the Platinum operating system. This includes stand-alone acquisition systems such as EAMs and NAMs, DAS units such as the Affinity and DM24SxEAM and digital instruments with built-in acquisition systems such as the 3TDE, 40TDE or 5TDE.s support data-signing with the CD1.1 protocol. This allows the data consumer to be assured of both the origin and the integrity of the data received. A hardware security module - the Spyrus Lynks™ card - is used to perform the signing algorithms. This ensures that the key used for signing the data cannot be recovered, even if the host platform is compromised.
Until firmware release 15781, data were signed using Digital Signature Algorithm (DSA), a well-known and widely-used algorithm. Platinum release 15781 introduces initial support for a new, stronger algorithm: Elliptic Curves and the associated Elliptic Curve Digital Signature Algorithm - ECDSA. Naturally, an EC-compatible Spyrus card is required to make use of this facility.
This document discusses aspects of this initial implementation and describes how to sign an arbitrary message - using either DSA or EC - and how to verify the signature using a Linux PC. This technique can be used to determine whether any given Spyrus card is EC-compatible or not.
Overview
The Spyrus Lynks™ HSM has a number of slots, each of which can store a different key. Until release 15781, all slots were essentially equivalent: they all operated in exactly the same way and the operator simply specified which slot they wished to use.
Under Platinum stable release 15781, the ninth slot now operates in a different way compared to the other slots. The other slots operate exactly as they did in previous versions.
Specifically: the ninth Spyrus Lynks™ slot now generates EC keys and EC signatures, rather than DSA keys and DSA signatures. If the underlying Spyrus Lynks™ hardware does not support EC keys or EC signatures, then the ninth slot will simply fail to operate. This also means that users can now test whether or not their Spyrus Lynks™ hardware supports EC keys and EC signatures.
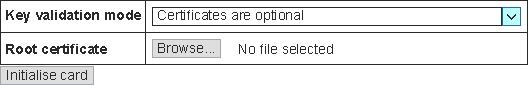
EC certificates and EC signature verification remain unsupported (as of release 15781), so please select Certificates are optional from the Key validation mode drop-down menu if you wish to continue using the ninth Spyrus Lynks™ slot:
If you do not know whether you have a Spyrus Lynks™ card fitted - or if you do but you are not making use of its ninth slot - then you will not notice any difference between Platinum stable release 15781 and Platinum stable release 15759.
Testing DSA signatures
This section describes how to get your Spyrus Lynks™ hardware to DSA-sign a message and, then, how to use a Linux PC to verify the DSA signature.
- On your Platinum unit, disable all instances of both data-out-cd11 and gdi2cd11 services, otherwise they will interfere with steps 2→5 below.
-
Delete all key pairs from your Spyrus Lynks™ hardware, then, generate a new DSA key pair in Slot 1:
DAS-123456 ~ # spyrus_util --init --sso-pin 1234 --pin 1234 WARNING: Initialising the card is DANGEROUS You will lose all the data stored on the card including any security credentials and certificates. These will need to be re-installed by a Site Security Officer. If you still wish to proceed enter "yes" at the prompt Proceed ? yes DAS-123456 ~ # spyrus_util --keygen --index 1 -----BEGIN PUBLIC KEY----- xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxx the DSA public key xxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx -----END PUBLIC KEY----- DAS-123456 ~ # -
Get the DSA public key from Slot 1 of your Spyrus Lynks™ hardware:
DAS-123456 ~ # spyrus_util --getkey --index 1 > dsa_pub.pem DAS-123456 ~ # -
Create the message to sign:
DAS-123456 ~ # echo -n "The quick brown fox jumps over the lazy dog" > msg.txt DAS-123456 ~ # -
Instruct your Spyrus Lynks™ hardware to DSA sign the message:
DAS-123456 ~ # spyrus_util --sign msg.txt --index 1 --binary > dsa_signature.bin DAS-123456 ~ # -
Copy the DSA public key, the message and the DSA signature from your Platinum unit to the Linux PC, then check that the DSA public key looks OK:
[you@yourlinuxpc ~]$ scp root@DAS-123456:/root/\{dsa_pub.pem,msg.txt,dsa_signature.bin\} . dsa_pub.pem msg.txt dsa_signature.bin [you@yourlinuxpc ~]$ openssl dsa -in dsa_pub.pem -pubin -text -noout read DSA key pub: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx: the DSA public key :xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx P: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx Q: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx G: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx [you@yourlinuxpc ~]$ -
Verify the DSA signature on your Linux PC using the DSA public key:
[you@yourlinuxpc ~]$ openssl dgst -sha1 -verify dsa_pub.pem -signature dsa_signature.bin msg.txt Verified OK [you@yourlinuxpc ~]$
This completes the procedure.
Testing EC signatures
This section describes how to get your Spyrus Lynks™ hardware to EC-sign a message and, then, how to use a Linux PC to verify the EC signature.
-
On your Platinum unit, disable all instances of both data-out-cd11 and gdi2cd11 services, otherwise they will interfere with steps 2→5 below.
-
Delete all key pairs from your Spyrus Lynks™ hardware, then, generate a new EC key pair in Slot 9 of your Spyrus Lynks™ hardware:
DAS-123456 ~ # spyrus_util --init --sso-pin 1234 --pin 1234 WARNING: Initialising the card is DANGEROUS You will lose all the data stored on the card including any security credentials and certificates. These will need to be reinstalled by a Site Security Officer. If you still wish to proceed enter "yes" at the prompt Proceed ? yes DAS-123456 ~ # spyrus_util --keygen --index 9 -----BEGIN PUBLIC KEY----- xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx the EC public key xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx -----END PUBLIC KEY----- DAS-123456 ~ # -
Get the EC public key from Slot 9 of your Spyrus Lynks™ hardware:
DAS-123456 ~ # spyrus_util --getkey --index 9 > ec_pub.pem DAS-123456 ~ # -
Create the message to sign:
DAS-123456 ~ # echo -n "The quick brown fox jumps over the lazy dog" > msg.txt DAS-123456 ~ # -
Instruct your Spyrus Lynks™ hardware EC sign the message:
DAS-123456 ~ # spyrus_util --sign msg.txt --index 9 --binary > ec_signature.bin DAS-123456 ~ # -
Copy the EC public key and the message and the EC signature from your Platinum unit to your Linux PC, then check that the EC public key looks OK:
[you@yourlinuxpc ~]$ scp root@DAS-123456:/root/\{ec_pub.pem,msg.txt,ec_signature.bin\} . ec_pub.pem msg.txt ec_signature.bin [you@yourlinuxpc ~]$ openssl ec -in ec_pub.pem -pubin -text -noout read EC key Private-Key: (256 bit) pub: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx: the EC public key :xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx: xx:xx:xx:xx:xx ASN1 OID: prime256v1 NIST CURVE: P-256 [you@yourlinuxpc ~]$ -
Verify the EC signature on your Linux PC using the EC public key:
[you@yourlinuxpc ~]$ openssl dgst -sha256 -verify ec_pub.pem -signature ec_signature.bin msg.txt Verified OK [you@yourlinuxpc ~]$
This completes the procedure.
